FIDO Alliance
The FIDO ("Fast IDentity Online") Alliance is an open industry association launched in February 2013 whose mission is to develop and promote authentication standards that help reduce the world’s over-reliance on passwords. FIDO addresses the lack of interoperability among strong authentication devices and reduces the problems users face creating and remembering multiple usernames and passwords.
 | |
| Founded | February 2013 |
|---|---|
| Headquarters | , |
| Website | fidoalliance |
Overview
FIDO supports a full range of authentication technologies, including biometrics such as fingerprint and iris scanners, voice and facial recognition, as well as existing solutions and communications standards, such as Trusted Platform Modules (TPM), USB security tokens, embedded Secure Elements (eSE), smart cards, and near field communication (NFC).[1] The USB security token device may be used to authenticate using a simple password (e.g. four-digit PIN) or by pressing a button. The specifications emphasize a device-centric model. Authentication over the wire happens using public-key cryptography. The user's device registers the user to a server by registering a public key. To authenticate the user, the device signs a challenge from the server using the private key that it holds. The keys on the device are unlocked by a local user gesture such as a biometric or pressing a button.
FIDO provides two types of user experiences depending on which protocol is used.[1] Both protocols define a common interface at the client for whatever local authentication method the user exercises.
Members
FIDO was founded by Agnitio, Infineon, Lenovo, Nok Nok Labs, PayPal and Validity Sensors.[2] By the end of September 2016, FIDO members totaled more than 260, including a board made up of Aetna, Alibaba Group, Amazon, American Express, ARM, Bank of America, BC Card, Broadcom, CrucialTec, Daon, Egis Technology, Feitian, Gemalto, Google, HYPR, Infineon, Intel, ING, Lenovo, MasterCard, Microsoft, Nok Nok Labs, NTT DoCoMo, NXP Semiconductors, Oberthur Technologies, PayPal, Qualcomm, RSA, Samsung Electronics, Synaptics, USAA, Visa, VMware, OneSpan, Yubico and Apple Inc representatives.[3] A full list of members is available on the official website.
Specifications
The following open specifications may be obtained from the FIDO web site.[4]
- Universal Authentication Framework (UAF)
- UAF 1.0 Proposed Standard (December 8, 2014)
- UAF 1.1 Proposed Standard (February 2, 2017)
- UAF 1.2 Review Draft (November 28, 2017)
- Universal 2nd Factor (U2F)
- U2F 1.0 Proposed Standard (October 9, 2014)
- U2F 1.2 Proposed Standard (July 11, 2017)
- FIDO 2.0 (contributed to the W3C on November 12, 2015)[5]
- FIDO 2.0 Proposed Standard (September 4, 2015)
- Client to Authenticator Protocol (CTAP)
- CTAP 2.0 Proposed Standard (September 27, 2017)
- CTAP 2.0 Implementation Draft (February 27, 2018)
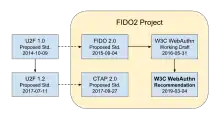
The U2F 1.0 Proposed Standard (October 9, 2014) was the starting point for a short-lived specification known as the FIDO 2.0 Proposed Standard (September 4, 2015). The latter was formally submitted to the World Wide Web Consortium (W3C) on November 12, 2015.[6] Subsequently, the first Working Draft of the W3C Web Authentication (WebAuthn) standard was published on May 31, 2016. The WebAuthn standard has been revised numerous times since then, becoming a W3C Recommendation on March 4, 2019.
Meanwhile the U2F 1.2 Proposed Standard (July 11, 2017) became the starting point for the Client to Authenticator Protocol 2.0 Proposed Standard, which was published on September 27, 2017. FIDO CTAP 2.0 complements W3C WebAuthn, both of which are in scope for the FIDO2 Project.
Milestones
- (2014-10-09) The U2F 1.0 Proposed Standard was released
- (2014-12-08) The UAF 1.0 Proposed Standard was released[7][8]
- (2015-06-30) The FIDO Alliance released two new protocols that support Bluetooth technology and near field communication (NFC) as transport protocols for U2F[9]
- (2015-09-04) The FIDO 2.0 Proposed Standard was released
- FIDO 2.0 Key Attestation Format
- FIDO 2.0 Signature Format
- FIDO 2.0 Web API for Accessing FIDO 2.0 Credentials
- (2015-11-12) The FIDO Alliance submitted the FIDO 2.0 Proposed Standard to the World Wide Web Consortium (W3C)[6][10]
- (2016-02-17) The W3C created the Web Authentication Working Group
- (2017-02-02) The UAF 1.1 Proposed Standard was released
- (2017-07-11) The U2F 1.2 Proposed Standard was released
- (2017-09-27) The Client To Authenticator Protocol 2.0 Proposed Standard was released
- (2017-11-28) The UAF 1.2 Review Draft was released
- (2018-02-27) The Client To Authenticator Protocol 2.0 Implementation Draft was released
See also
References
- "Specifications Overview". FIDO Alliance. Retrieved 31 October 2014.
- "History of FIDO Alliance". FIDO Alliance. Retrieved 2019-08-30.
- "FIDO Alliance Members". FIDO Alliance. Retrieved 2019-01-03.
- "Download Specifications". FIDO Alliance. Retrieved 13 February 2019.
- "FIDO 2.0: Overview". fidoalliance.org. Retrieved 2021-01-21.
- "Submission Request to W3C: FIDO 2.0 Platform Specifications 1.0". World Wide Web Consortium (W3C). Retrieved 12 February 2019.
- "FIDO 1.0 Specifications Published and Final". FIDO Alliance. Retrieved 31 December 2014.
- "Computerworld, December 10, 2014: "Open authentication spec from FIDO Alliance moves beyond passwords"". Computerworld. Retrieved 10 December 2014.
- "eWeek, July 1, 2015: "FIDO Alliance Extends Two-Factor Security Standards to Bluetooth, NFC"". eWeek. Retrieved 1 July 2015.
- "W3C Member Submission 20 November 2015: FIDO 2.0: Web API for accessing FIDO 2.0 credentials". W3C. Retrieved March 14, 2016.